SocketX Server On-Premise Deployment
Introduction
SocketX Server is an end-to-end encryption system that protects all WebSocket traffic with next-generation application data security. It acts as a proxy server in front of your backend WebSocket infrastructure, communicating with a SocketX Client to encode and decode all WebSocket frames. The server is highly customizable and supports integration with other services through custom adapters.
Below is an example architecture where a client application communicates with a SocketX Server, which then proxies decoded WebSocket traffic to backend services:
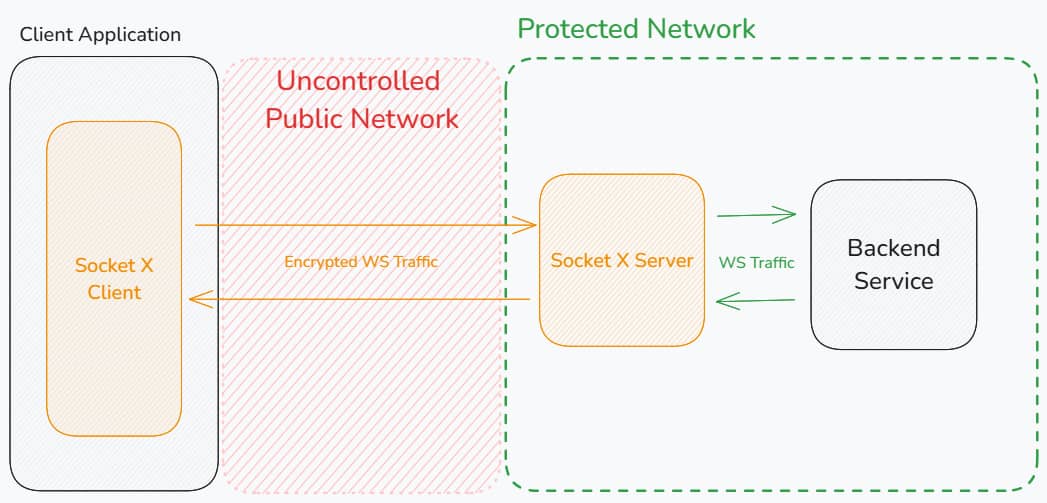
Prerequisites
Technical Requirements
- A web or mobile application project that communicates with a backend service over WebSocket.
- Docker installed and running on your system.
- AWS CLI installed.
Skills and Knowledge
- Familiarity with Docker and/or Kubernetes.
- Basic knowledge of configuring containerized services.
Credentials
- An AWS Access Key ID and AWS Secret Access Key provided by Eclypses to access the private container repository.
Deployment Options
SocketX Server is provided as a Docker image and can be deployed on-premise using:
- Docker Run
- Docker Compose
- Kubernetes
- Other container runtimes (e.g., Podman, Docker Swarm, K3s)
1. Configure AWS CLI Access
You must configure a new AWS CLI profile using the credentials provided by Eclypses.
aws configure --profile eclypses-customer-on-prem
When prompted:
- AWS Access Key ID: Enter the ID provided by Eclypses.
- AWS Secret Access Key: Enter the secret key provided.
- Default region name: us-east-1
- Default output format: json
2. Pull the Docker Image
Authenticate Docker with the Eclypses ECR repository:
- bash
- PowerShell
aws ecr get-login-password \
--region us-east-1 \
--profile eclypses-customer-on-prem \
| docker login --username AWS \
--password-stdin 321186633847.dkr.ecr.us-east-1.amazonaws.com
aws ecr get-login-password `
--region us-east-1 `
--profile eclypses-customer-on-prem `
| docker login --username AWS `
--password-stdin 321186633847.dkr.ecr.us-east-1.amazonaws.com
Then pull the image:
docker pull 321186633847.dkr.ecr.us-east-1.amazonaws.com/customer/on-prem/socketx-server-go:1.0.0
Server Configuration
SocketX Server is configured using environment variables.
Required Variables
DOMAIN_MAP- JSON string mapping domains. Wildcards are supported.
Optional Variables
LISTEN_HOST- Default:0.0.0.0.LISTEN_PORT- Default:8080.LOG_LEVEL- One of debug, info, warn, error, panic, off. Default:info.WS_READ_BUFFER_SIZE- Websocket read buffer size in bytes. Default:1024.WS_WRITE_BUFFER_SIZE- Websocket write buffer size in bytes. Default:1024.
Minimal Example
DOMAIN_MAP={"*":"ws://service.com"}
Full Example
DOMAIN_MAP={"*":"ws://example.com"}
LISTEN_HOST=0.0.0.0
LISTEN_PORT=8080
LOG_LEVEL=info
WS_READ_BUFFER_SIZE=2048
WS_WRITE_BUFFER_SIZE=2048
Deployment Steps
Option A: Docker Run
- bash
- PowerShell
docker run --rm -it \
--name socketx \
-p 8080:8080 \
-e DOMAIN_MAP={"*":"ws://example.com"} \
321186633847.dkr.ecr.us-east-1.amazonaws.com/customer/on-prem/socketx-server-go:1.0.0
docker run --rm -it `
--name socketx `
-p 8080:8080 `
-e DOMAIN_MAP={"*":"ws://example.com"} `
321186633847.dkr.ecr.us-east-1.amazonaws.com/customer/on-prem/socketx-server-go:1.0.0
Option B: Docker Compose
version: "3.8"
services:
socketx:
image: 321186633847.dkr.ecr.us-east-1.amazonaws.com/customer/on-prem/socketx-server-go:1.0.0
ports:
- "8080:8080"
environment:
- DOMAIN_MAP={"*":"ws://example.com"}
Option C: Kubernetes
apiVersion: apps/v1
kind: Deployment
metadata:
name: socketx
spec:
replicas: 2
selector:
matchLabels:
app: socketx
template:
metadata:
labels:
app: socketx
spec:
containers:
- name: socketx
image: 321186633847.dkr.ecr.us-east-1.amazonaws.com/customer/on-prem/socketx-server-go:1.0.0
ports:
- containerPort: 8080
env:
- name: DOMAIN_MAP
value: '{"*":"ws://example.com"}'
---
apiVersion: v1
kind: Service
metadata:
name: socketx-service
spec:
type: LoadBalancer
selector:
app: socketx
ports:
- protocol: TCP
port: 80
targetPort: 8080
kubectl apply -f socketx-deployment.yaml
kubectl get all
kubectl delete -f socketx-deployment.yaml
Testing & Health Checks
-
Monitor container logs for startup messages:
SocketX server starting
-
Test echo route:
curl http://<SOCKETX_HOST_OR_IP>:<PORT>/api/socketx-echo?msg=test
Expected response:
{
"echo": "test",
"time": "<timestamp>"
}
Troubleshooting
- Invalid Configuration
- Check logs for missing/invalid environment variables.
- SocketX unreachable
- Verify firewall, networking, or Kubernetes service configuration.
Security
- No sensitive data stored in the container.
- No root privileges required.
Compliance Coverage Summary
Purpose:
- Demonstrate that SocketX server logs serve as verifiable, cryptographically-anchored compliance evidence across data-layer security, auditability, and AI-governance frameworks.
Governance Domains and Control Alignment
Confidentiality - cryptographic enforcement and keyless privacy
Fields: event_type, payload_sha256, eeid, mte_kyber_strength
Coverage: NIST SC-13 · FedRAMP SC-13 · SOC 2 CC6.1 · EU AI Act Art 10(3)
Integrity - proof of data fidelity and replay prevention
Fields: payload_sha256, cid, duration_ms
Coverage: NIST SI-7 · FedRAMP SI-7 · SOC 2 CC7.4 · EU AI Act Art 15(2-3)
Availability - continuous, timestamped operational visibility
Fields: time, audit.duration_seconds, close_reason
Coverage: NIST AU-12 · FedRAMP AU-12 · SOC 2 CC7.2
Accountability & Traceability - correlation, provenance, and actor identification
Fields: cid, user_agent, audit
Coverage: NIST AU-10 · FedRAMP AU-6(3) · SOC 2 CC7.2 · EU AI Act Art 13
AI Governance & Transparency - mandatory operational logging for AI workloads
Fields: event_type=encryption/decryption, config (version & Kyber params)
Coverage: EU AI Act Art 10 · 13 · 15
Framework Coverage Summary
| Framework | Primary Control Families Satisfied | Estimated Coverage |
|---|---|---|
| NIST 800-53 r5 | AU-2, AU-3, AU-6, AU-10, SI-4, SI-7, SC-13 | ≈ 85 % |
| FedRAMP (Moderate / High) | AU, SI, SC, CM families + FIPS 140-3 crypto enforcement | ≈ 80 % |
| SOC 2 Type II | CC6.1, CC6.2, CC7.2, CC7.3, CC7.4 | ≈ 90 % |
| EU AI Act (2024) | Art 10 (Data Governance), Art 13 (Transparency), Art 15 (Traceability) | 100 % |
Structural Compliance
| Element | Present in Log | Compliance Purpose |
|---|---|---|
Timestamp (time) | True | Required for tamper-proof chronology (NIST 800-92 §4.1) |
Severity (level) | True | Mandatory classification for audit triage |
Event Type (event_type) | True | Enables control-family mapping (SI-4, AU-2, AU-3) |
Correlation ID (cid) | True | Provides end-to-end traceability per transaction (SOC 2 CC7.2) |
Payload Integrity Hash (payload_sha256) | True | Cryptographic proof of data fidelity (NIST 800-53 SI-7, EU AI Act Art. 10 §3 fidelity) |
Cryptographic Metrics (duration_ms, payload_size_bytes) | True | Enables deterministic crypto performance verification |
Configuration Snapshot (config block) | True | Required system-baseline record (FedRAMP AC-17, CM-6) |
User/Agent Info (user_agent) | True | Maps to identity and access logging (AU-6, EU AI Act Art. 13 transparency) |
Session Audit Block (audit) | True | Provides closure evidence (ISO 27001 A.12.4.1 audit trail completeness) |
Cryptographic Enforcement Layer (CEL) Alignment
Each MTE encryption/decryption event includes:
- One-time payload encoding (
eeid= event entropy ID) - SHA-256 verification token
- Runtime duration (in ms)
Together these create verifiable, immutable evidence of cryptographic enforcement for every data transaction - fulfilling CEL audit-trace requirements for:
- Data Fidelity (tamper-proof chain of custody)
- Replay Prevention (unique
eeid+ transientcid) - Quantum-resistant handshake traceability (Kyber 512 param in
config)
Standards Mapping
| Framework / Standard | Relevant Clauses Satisfied by Log |
|---|---|
| NIST 800-92 / 800-53 rev5 | AU-2, AU-3, AU-6, SI-4 (logging completeness & incident correlation) |
| FedRAMP Moderate / High | AU-2(a-d), AU-6(1), SI-7(1-3), SC-13 (cryptographic logging, FIPS 140-3 context) |
| SOC 2 Type II | CC6.1 (Change mgmt), CC7.2 (Monitoring), CC7.3 (Incident detection) |
| ISO 27001:2022 | A.12.4.1 (Event logging), A.8.16 (Cryptographic controls) |
| EU AI Act (draft 2024 voted) | Art. 10 (Data governance), Art. 13 (Transparency & traceability), Art. 15 (Logging of operations) |
Key Compliance Advantages
- Cryptographic Enforcement Layer (CEL): every payload's encrypt/decrypt event is FIPS-140-3 validated and recorded with runtime metrics.
- Deterministic Evidence:
duration_ms+payload_size_bytesprovide measurable cryptographic performance proofs. - Tamper-Evident Logging: SHA-256 hashes + unique entropy IDs (
eeid) guarantee payload fidelity. - AI-Governance Ready: fully meets EU AI Act logging mandates for explainability, lineage, and traceability.
- Audit Simplified: logs integrate directly into Prometheus, Grafana, or SIEMs with control-family correlation.
SocketX / MTE logging is not mere telemetry - it is cryptographic compliance evidence. Each record proves that data was encrypted, verified, and audited in real time, meeting the governance, traceability, and AI-risk requirements of all major frameworks without exposing any keys or payload content.
Costs
Private infrastructure costs (VMs, storage, networking) are customer-managed.
Maintenance
Routine Updates
- Updated container images are distributed through Eclypses.
Fault Recovery
- Relaunch the SocketX container; clients will automatically re-pair.
Support
For assistance, contact Eclypses Support:
📧 customer_support@eclypses.com
🕒 Monday-Friday, 8:00 AM-5:00 PM MST (excluding holidays)